For example use an off-site cloud storage service with on-site network-attached storage NAS. Incident response IR is a structured methodology for handling security incidents breaches and cyber threats.
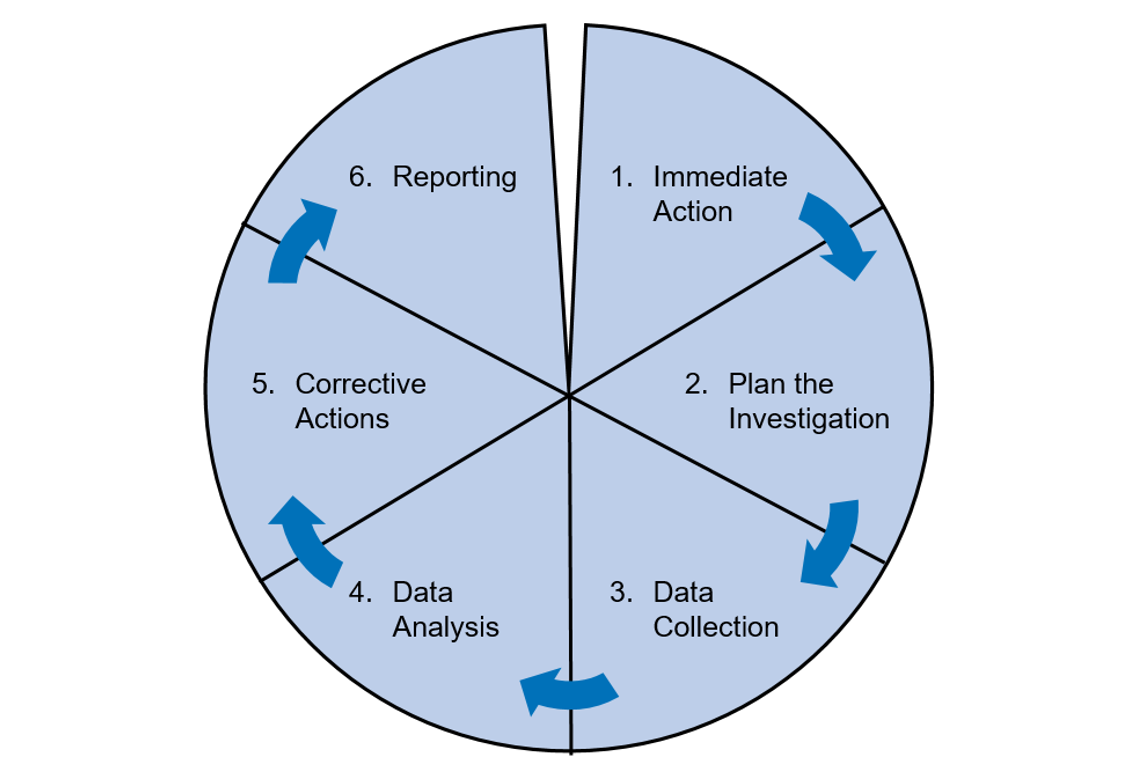
Six Steps For Successful Incident Investigation Risktec
If Event Then Consequences.

. High- priority and low-priority with a unique ringtone and persistent alerts to ensure critical messages are. One simple and powerful way to do this is to use the If-Then Risk Statements. Obtaining the Correct Information.
Describe two ways that status data is used Status data are details that are used from CIS 202 at ECPI University. Excerpt from Essay. Data collection thus has a proactive accident preven-tion function even.
Many terms are used to describe these approaches including real time evaluations rapid feedback evaluation rapid evaluation methods rapid-cycle evaluation and rapid appraisal. The BJS established the NCVS to provide previously unavailable information about crime including crime not reported to police victims and offenders. If Event Then Consequences.
DHS will continue to make more datasets available as we follow our process for identifying and approving the release of high-value datasets. If you want to back up the data on your PC here are five ways you can do so. If you have ideas or suggestions for new datasets or datasets you have seen on one of the DHS web sites you can email your ideas to CDOD_HQhqdhsgov.
The maximum volume of oil estimated to have been spilled during the Deepwater Horizon BP incident. An alert roster is a list of individuals within the company who must be notified in the event of an incident. Mobile incident management gives incident responders full visibility into the incident and have quick easy ways to respond so they can take quick action Priority alerting allows the user to send messages in two different formats.
Its response is uncertain. Include units b Describe. Second the two programs measure an overlapping but nonidentical set of crimes.
A Rapid Evaluation is an approach that uses multiple evaluation methods and techniques to quickly and systematically collect data when time or resources are limited. 10 things you can do to protect your data. Define the term incident as used in the context of IRP How is it related to the from ITIA 1400 at Macomb Community College.
This method is used if the field of inquiry is wide. An alert roster is a document that includes contact information on every individual to be notified on the occasion of an actual incident. Information can be collected from the educated persons only.
This can either be done accidentally or deliberately. In a sequential roster a contact person is required to call each and every individual on the roaster. The state of the system and the actions that occurred at the time the people directly and indirectly involved the tools equipment materials and fixtures directly connected the time the accident or incident occurred.
Operating systems and applications can always be reinstalled but your data is unique--making it the most important thing on your computer or network. However data loss has been used interchangeably with data breach since cybercriminals dont always give your information back or corrupt it in the hacking process. There is uniformity in the data because informants are directly involved Demerits.
Uniform Crime Reports and the National Incident-Based Reporting System Two major sources of crime statistics commonly used in the United States are the Uniform Crime Reports UCR and the National Incident-Based Reporting System NIBRS. Simply put data exfiltration indicates the movement of sensitive data from inside the organization to outside without authorization. Crime Data Sources in the United States The collection of crime data in the United States is carried out through different approaches including Uniform Crime Reports and the National Incident-Based Reporting System which also act as the two primary sources of crime data for crime reporting.
Using the data in the graph above determine. 1 point for identifying a specific number 185 million gallons and 199 million gallons. Facts regarding what occurred immediately after the incident.
An alert message is a scripted notification that provides just enough information for responders to know the status of the incident and what portion of the incident response plan they need to implement. Anecdotal evidence comes in the form of retellings of events from parties involved in the investigation. The NCVS includes crimes both reported and not reported to law enforcement.
Each method has its pros and cons. Describe the two ways they can be used. Malware infections rapidly spread ransomware can cause catastrophic damage and compromised accounts can be used for privilege escalation giving attackers access to more sensitive assets.
Sources of Crime Data. Data loss is distinct from data unavailability which is primarily caused by power outages and from a data breach which refers to your data being stolen. This information is used to prevent reoccurrence of similar accidents and to identify the underlying causes that may give rise to new types of accidents in the future.
If the electrical system is not installed per the specifications then there may be additional cost and an adverse impact to the schedule. Keeping incident records provides a broad spectrum of information about the circumstance as well as helps establish a better course of action for future incident prevention. A well-defined incident response plan IRP allows you.
However data is raw information with no judgment attached. That way if either fails you still have a backup. There are two ways to activate an alert roster.
The data obtained from these sources are used for research. Supplementary questions cannot be asked as questions are fixed. Data forms the basis for evidence so theres a lot of overlap between the two concepts.
While not clear enough evidence to use in court this kind of data can be useful for increasing credibility by drawing parallels when there isnt enough clear-cut information to prove something in a workplace investigation. If questionnaire is tough it may not be responded. TWO environmental problems that can result from oil spills in coastal areas.
Evidence is when data is used to try to prove. Sequentially and hierarchically. For the ultimate in safety choose two and use them concurrently.
This can either be done accidentally or deliberately. There are many ways of organizing the information but all processes should rely as much as possible on factual data rather than inference. Facts of the incident itself Investigate.

Incident Management It Process Wiki

Remote Sensing Vector Illustration Satellite Data Wave Acquisition Scheme Educational Active And Passive Inf Remote Sensing Remote Sensing And Gis Satellites

Root Cause Analysis Software Excel Tools Excel Tutorials Analysis Excel
0 Comments